Elastic Container Registry
AIM -> Users
Choose "Programmatic access" -> Next
Choose "Attach existing policies directly" -> "Create Policy"
And add next:
Read all repo:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"ecr:GetLifecyclePolicyPreview",
"ecr:GetDownloadUrlForLayer",
"ecr:BatchGetImage",
"ecr:DescribeImages",
"ecr:DescribeRepositories",
"ecr:ListTagsForResource",
"ecr:ListImages",
"ecr:BatchCheckLayerAvailability",
"ecr:GetLifecyclePolicy",
"ecr:GetRepositoryPolicy"
],
"Resource": "*"
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": "ecr:GetAuthorizationToken",
"Resource": "*"
}
]
}
############### Read only one repo ##################
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"ecr:GetLifecyclePolicyPreview",
"ecr:GetDownloadUrlForLayer",
"ecr:BatchGetImage",
"ecr:DescribeImages",
"ecr:DescribeRepositories",
"ecr:ListTagsForResource",
"ecr:ListImages",
"ecr:BatchCheckLayerAvailability",
"ecr:GetLifecyclePolicy",
"ecr:GetRepositoryPolicy"
],
"Resource": "arn:aws:ecr:eu-west-1:111111111111:repository/artem-repo"
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": "ecr:GetAuthorizationToken",
"Resource": "*"
}
]
}
eu-west-1 — region
111111111111 — registry ID
artem-repo — repository name
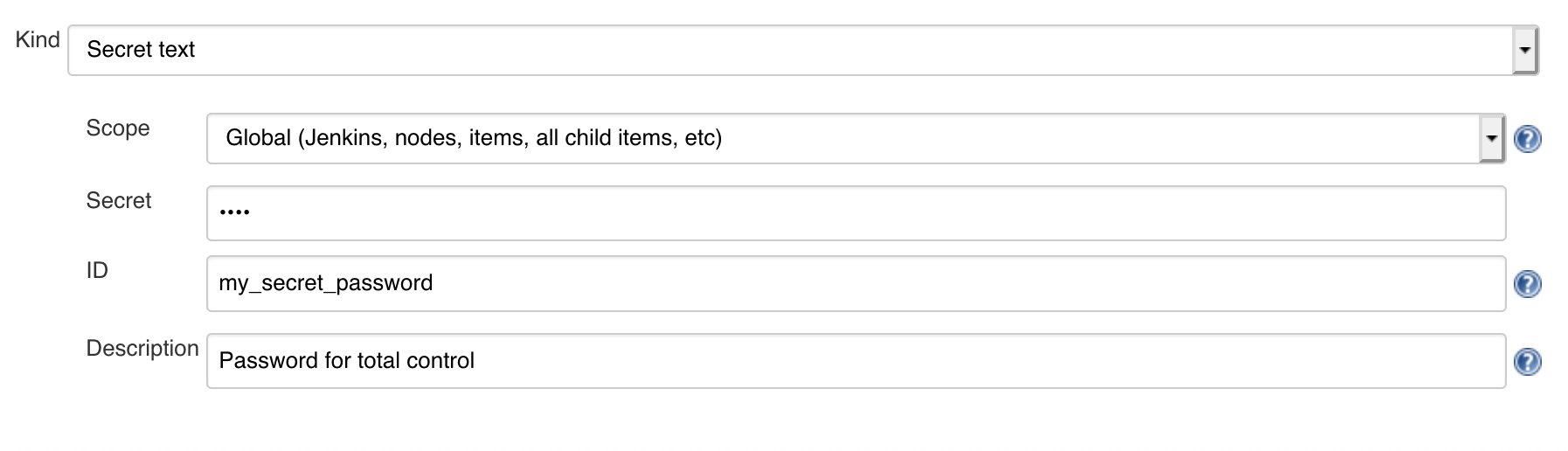
Save "Access key ID" and "Secret access key"
XXXXXXXXXXXXXXXXXXXX
YYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYY
sudo apt update sudo apt install make
Для следующего шага должен быть установлен Docker
cd /tmp && git clone https://github.com/awslabs/amazon-ecr-credential-helper.git cd amazon-ecr-credential-helper && sudo make docker sudo cp -a bin/local/docker-credential-ecr-login /usr/bin/ mkdir ~/.docker/ vim ~/.docker/config.json
And add next:
{
"credsStore": "ecr-login"
}
Если не установлен AWS-Cli
sudo apt install awscli aws configure
И указываем "Access key ID" and "Secret access key"